In the realm of digital communication, privacy concerns have taken center stage. WhatsApp, a ubiquitous messaging platform, has responded to these concerns by implementing end-to-end encryption, a transformative technology that safeguards user data from prying eyes. In this comprehensive guide, we delve into the intricacies of WhatsApp’s end-to-end encryption, empowering you with the knowledge to protect your conversations and ensure your digital privacy.
WhatsApp’s end-to-end encryption is a robust mechanism that ensures that only the sender and intended recipient can access the content of messages, calls, and media shared through the platform. This encryption process is like a digital fortress, preventing unauthorized parties, including WhatsApp itself, from intercepting or deciphering your communications.
Introduction to WhatsApp’s End-to-End Encryption
End-to-end encryption (E2EE) is a cryptographic technique that ensures that only the sender and intended recipient can read the contents of a message. In WhatsApp’s case, this means that no one else, not even WhatsApp itself, can access the content of your messages.
WhatsApp first implemented E2EE in April 2016, making it one of the first major messaging apps to do so. Since then, E2EE has become an essential feature for many users who value their privacy.
Importance of End-to-End Encryption
E2EE is important for user privacy because it prevents third parties from accessing the content of your messages. This is especially important for sensitive conversations, such as those involving financial information, personal data, or confidential business matters.
Without E2EE, third parties could potentially intercept and read your messages, which could have serious consequences for your privacy and security.
How End-to-End Encryption Works on WhatsApp
WhatsApp employs a robust end-to-end encryption protocol to safeguard user messages and calls. This advanced security measure ensures that only the sender and recipient can access the content of their communications, preventing unauthorized parties from intercepting or deciphering them.End-to-end encryption involves a complex cryptographic process that utilizes public and private keys to encrypt and decrypt messages.
Each WhatsApp user possesses a unique pair of keys: a public key and a private key. The public key is shared with other users, while the private key is kept secret and stored securely on the user’s device.When a message is sent, WhatsApp generates a random session key and encrypts the message using the recipient’s public key.
The encrypted message is then sent to the recipient, who uses their private key to decrypt it. This process ensures that the message remains encrypted throughout its transmission and can only be decrypted by the intended recipient.
Visual Representation of the Encryption Process
The following diagram illustrates the end-to-end encryption process on WhatsApp: [Diagram of the encryption process: User A sends a message to User B. User A’s device encrypts the message using User B’s public key. The encrypted message is sent to User B’s device.
User B’s device decrypts the message using User B’s private key.] As depicted in the diagram, the message is encrypted on User A’s device and decrypted on User B’s device, ensuring that the message remains secure during transmission.
Benefits of End-to-End Encryption on WhatsApp
End-to-end encryption on WhatsApp provides several significant advantages for users, including enhanced privacy and security.
By encrypting messages, end-to-end encryption prevents eavesdropping and data breaches. Only the sender and intended recipient can access the message content, making it more difficult for unauthorized parties to intercept and read private conversations.
Protection from Eavesdropping
End-to-end encryption protects WhatsApp users from eavesdropping by encrypting messages in a way that makes them unreadable to anyone other than the sender and intended recipient. This prevents third parties, such as hackers, governments, or even WhatsApp itself, from accessing the content of private conversations.
Protection from Data Breaches
End-to-end encryption also protects WhatsApp users from data breaches. In the event of a data breach, encrypted messages remain protected, as the encryption keys are not stored on WhatsApp’s servers. This makes it much more difficult for unauthorized parties to access and decrypt private conversations, even if they gain access to WhatsApp’s servers.
Examples of End-to-End Encryption Protecting User Privacy
- In 2019, WhatsApp end-to-end encryption played a crucial role in protecting the privacy of journalists and activists in Hong Kong during the anti-government protests. Encrypted messages allowed them to communicate securely and share sensitive information without fear of interception.
- In 2021, end-to-end encryption on WhatsApp was credited with protecting the privacy of healthcare workers in India during the COVID-19 pandemic. Encrypted messages allowed them to share patient information and coordinate care securely.
Limitations of End-to-End Encryption on WhatsApp
While end-to-end encryption provides a high level of security for WhatsApp users, it does have some limitations that can affect its functionality and effectiveness.
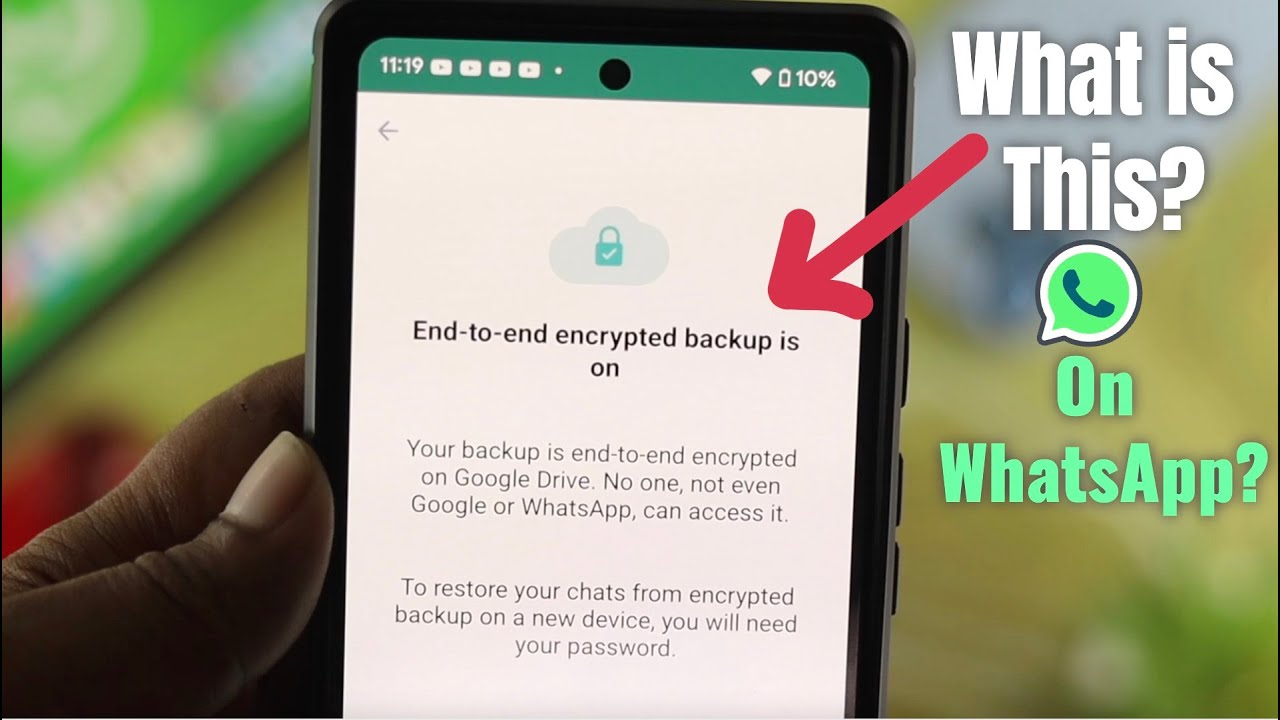
One limitation is that end-to-end encryption can impact the functionality of certain WhatsApp features, such as message backups. When messages are backed up to iCloud or Google Drive, they are not protected by end-to-end encryption, making them potentially accessible to unauthorized individuals.
Additionally, end-to-end encryption does not protect messages that are forwarded to non-WhatsApp users.
Situations Where End-to-End Encryption May Not Be Effective
- When messages are backed up to iCloud or Google Drive.
- When messages are forwarded to non-WhatsApp users.
- When WhatsApp is used on a device that has been compromised by malware or spyware.
- When a user’s WhatsApp account is hacked or compromised.
Conclusion
WhatsApp’s end-to-end encryption provides robust protection for user privacy. By encrypting messages before they leave the sender’s device and decrypting them only on the recipient’s device, it ensures that messages remain confidential and inaccessible to third parties, including WhatsApp itself.End-to-end
encryption is crucial for protecting sensitive conversations, personal data, and financial information. It empowers users with the assurance that their communications are secure and private. By using end-to-end encryption on WhatsApp and other messaging platforms, users can safeguard their privacy and communicate with confidence.
Final Conclusion
In conclusion, WhatsApp’s end-to-end encryption stands as a cornerstone of digital privacy, providing users with the assurance that their conversations remain confidential and secure. By embracing this encryption technology, we not only protect our personal data but also contribute to a more secure and trustworthy digital landscape.
As technology continues to evolve, it is imperative that we stay informed about the privacy features available to us and utilize them to safeguard our online interactions.
FAQ Summary
Is end-to-end encryption enabled by default on WhatsApp?
Yes, end-to-end encryption is automatically enabled for all WhatsApp users, ensuring that all messages, calls, and media shared through the platform are protected by default.
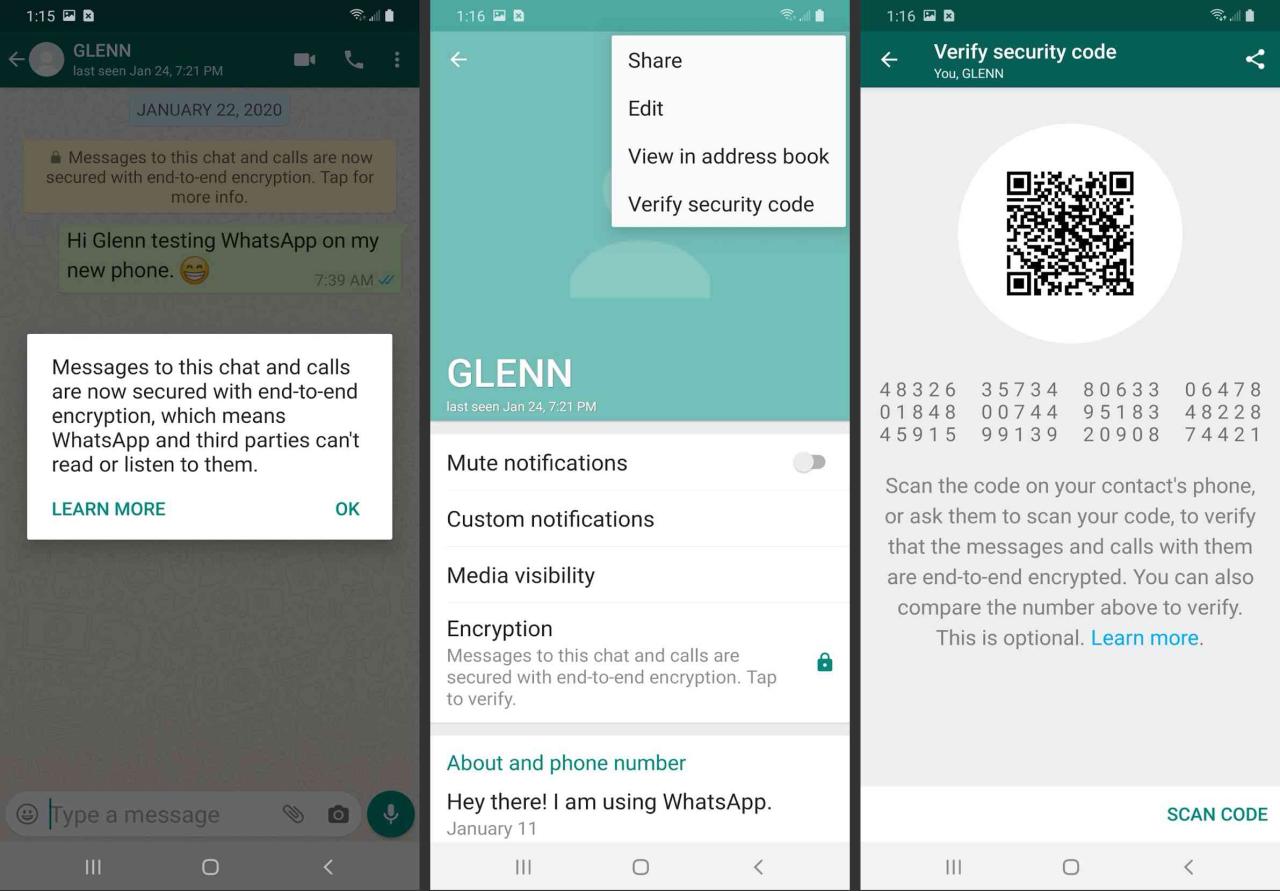
Can I verify if end-to-end encryption is working properly?
To verify end-to-end encryption, you can compare the security code displayed in your chat with the recipient. If the codes match, end-to-end encryption is active.
Does end-to-end encryption affect the functionality of WhatsApp?
End-to-end encryption does not significantly impact WhatsApp’s functionality. However, certain features, such as message forwarding, may be limited to protect the privacy of encrypted messages.



